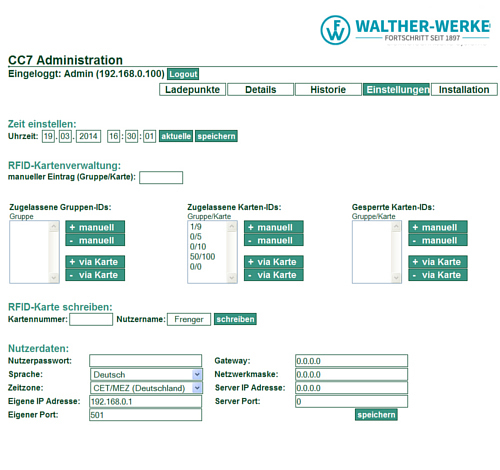
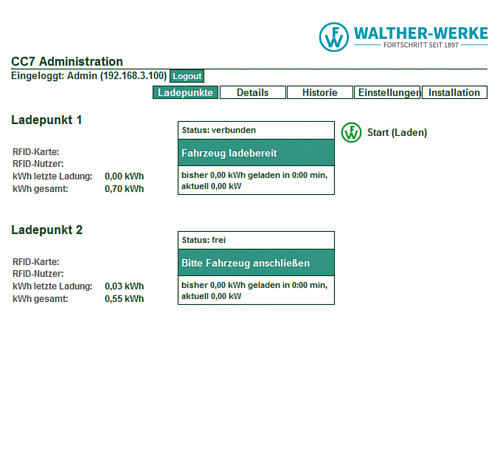
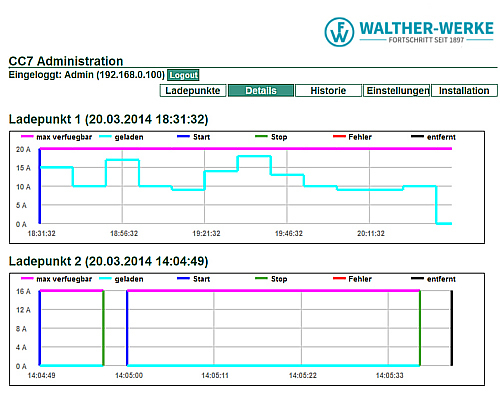
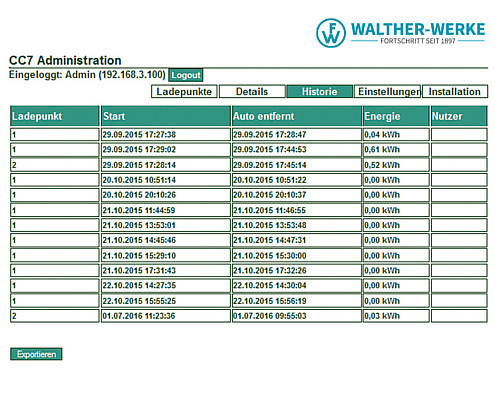
Our PRO versions are especially suitable for all settlement requirements or the combination of multiple operating methods for any charging station or system control. Operation is performed through intuitive user interactions via the touchscreen monitor. This allows cross-system settlement methods such as StromTicket, Ladenetz, Hubject and so on to be used.